Smartphones have become our constant companions, storing sensitive personal information, contacts, and even financial details. With the increasing sophistication of spyware, it’s more important than ever to know how to detect and remove these hidden threats. In this guide, we’ll walk you through How to Spot and Remove Spyware from Your Phone safely, using simple language and actionable steps. We’ll also share a real-life story about My Friend Sarah, who noticed her phone acting oddly, and explain how you can protect yourself from similar risks.
Understanding Spyware on Mobile Devices
Spyware is software that covertly gathers information from your device without your consent. It can monitor your communications, track your location, and even record your activities—all while hiding in plain sight.
What is Spyware?
Spyware is security threat that can download on your smartphone without your knowledge and its primary purpose is to grab data like passwords, contact lists and other personal information. Spyware usually comes in the disguise of an application or is hidden in the system processes and can be quite difficult to detect by normal users, and sometimes even by experienced users.
For a more detailed look into the technical aspects and evolution of spyware, check out this comprehensive research report from UCSB, which explores the methods used by spyware like Pegasus.

How Spyware Affects Your Phone
When spyware infiltrates your device, you may notice various symptoms:
- Battery Drain: Spyware can run background processes that deplete your battery faster.
- Performance Issues: Your phone may slow down or crash unexpectedly.
- Data Usage Spikes: Unexplained data transfers can be a sign that your phone is sending information to a remote server.
- Unexpected Ads: Pop-up ads or unusual notifications are often red flags.
Understanding these indicators is the first step to safeguarding your privacy.
Signs Your Phone May Be Infected
Before diving into removal methods, it’s essential to know the common signs of spyware infection. Recognizing these symptoms early can prevent further data loss and protect your personal information.
Unusual Battery Drain
One of the most common symptoms is a sudden decrease in battery life. Spyware runs processes in the background that use up processing power and battery. If you notice that your phone’s battery is depleting much faster than usual, it might be a sign of hidden surveillance software.
Unexpected Pop-Up Ads and Crashing Apps
If your apps start crashing unexpectedly or if you see random pop-up ads, it might be because spyware is trying to display information or prompt you to click on malicious links. Sarah, a regular smartphone user, experienced this first-hand. She found her battery draining faster than normal, her apps crashing without warning, and unwanted pop-up ads appearing frequently. Her experience is not unique, and it serves as a cautionary tale for many.
How to Detect Spyware on Your Phone

Detection can be achieved through a combination of automated tools and manual inspection techniques. The goal is to identify any unusual behavior and pinpoint suspicious applications or processes.
Using Automated Tools
There are several reputable security apps that can help scan your device for spyware. These tools analyze app permissions, monitor network traffic, and check for signs of hidden malware. Some popular options include:
- ProtectStar Anti-Spy: This tool scans for abnormal behavior using both memory and APK inspections. It supports both Android and iOS devices.
- Certo Mobile Security: Known for its full-disk scans, Certo Mobile Security can help detect spyware that may have evaded other methods.
- iVerify Basic: An iOS-focused app that examines memory usage to spot suspicious activity.
Below is a table summarizing some of the leading security applications based on recent studies:
| Application | Detection Rate | Forensic Scan | Real-Time Blocking | Platforms |
|---|---|---|---|---|
| Certo Mobile Security | 99.2% | Full disk | Yes | Android Only |
| ProtectStar Anti-Spy | 98.7% | Memory + APK | Yes | Android & iOS |
| iVerify Basic | 97.4% | Memory | No | iOS Focused |
These tools use modern scanning methods and are frequently updated to deal with emerging threats. Their high detection rates offer a strong line of defense against the latest spyware.
Manual Inspection Techniques
While automated tools are effective, there are also manual methods you can use to detect spyware. Follow these steps to conduct a basic inspection:
- Boot into Safe Mode: Safe Mode disables third-party apps, making it easier to spot any anomalies. On Android, press and hold the Power and Volume Down buttons. For iOS, follow the specific guidelines for your model.
- Review Running Processes: Use commands like
adb shell ps -Aon Android to see all active processes. Look for any processes with names that seem unfamiliar or suspicious. - Check Proxy Settings: Spyware may redirect your network traffic through a proxy server. Go into your network settings and ensure no unknown proxies are configured.
- Audit App Permissions: Compare the permissions requested by your apps with what they actually need. If an app is asking for excessive permissions, it might be a red flag.
For more detailed instructions, refer to this step-by-step guide on manual spyware removal from the tech community.
How to Spot and Remove Spyware from Your Phone Step-by-Step
Once you have detected spyware on your device, it’s important to act quickly to remove it. Below is a clear, step-by-step guide to help you eliminate spyware from your phone.
Step 1: Boot into Safe Mode
Why?
Safe Mode allows you to run your phone with only the essential apps and services, preventing any malicious software from running.
How to Do It:
- Android: Press and hold the Power and Volume Down buttons simultaneously.
- iOS: Follow the specific instructions for your device model.
Step 2: Uninstall Suspicious Apps
Go to your app manager and look for any applications that you do not remember installing or that request unusual permissions. Uninstall these apps immediately.
Step 3: Run a Full Device Scan
Use a trusted security app like ProtectStar Anti-Spy or Certo Mobile Security to run a full scan of your device. This will help identify any remaining malicious components.
Step 4: Remove Residual Files
After uninstalling the suspicious apps, clear your cache and data for all apps. This step removes any temporary files that spyware might have left behind.
Step 5: Reset Network Settings
Spyware can alter your network settings to redirect your data. Reset your network settings to default to ensure that no proxies or unusual configurations remain.
Step 6: Factory Reset (If Necessary)
If the spyware persists after following the previous steps, perform a factory reset. Remember to back up your important data before doing so, as this step will erase all content on your device.
Step 7: Post-Removal Validation
After removing the spyware, it’s important to verify that your phone is clean. Use network monitoring tools like Wireshark to check for any abnormal data traffic, and consider running another full scan using your security app.
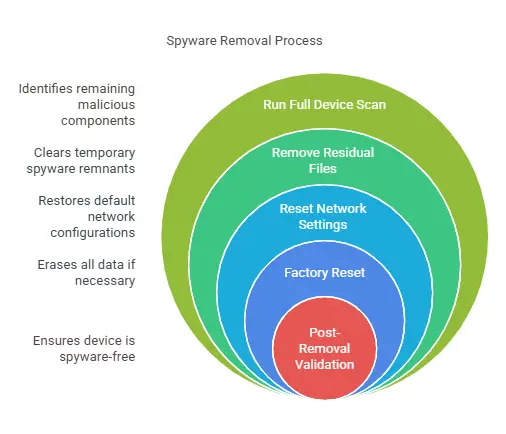
Below is a simplified checklist to guide you through the process:
| Step | Action Taken | Outcome |
|---|---|---|
| Boot into Safe Mode | Disable third-party apps | Reduced risk of spyware interference |
| Uninstall Suspicious Apps | Remove unknown or suspicious apps | Eliminated potential spyware sources |
| Run a Full Device Scan | Use a trusted security tool | Identify and isolate remaining spyware components |
| Remove Residual Files | Clear cache and temporary files | Clean out remnants of spyware |
| Reset Network Settings | Restore default network configurations | Ensure no malicious redirections are in place |
| Factory Reset (If Necessary) | Backup data and reset device | Complete removal of persistent threats |
| Post-Removal Validation | Monitor network traffic and re-scan the device | Confirm that the device is secure |
Following this checklist can help ensure that your device is thoroughly cleansed of spyware.
Preventing Future Spyware Infections

Taking preventive measures is just as important as removing spyware after it’s been detected. Here are some practical tips to keep your phone secure in the future.
Best Practices for Mobile Security
- Download Apps from Trusted Sources:
Only install apps from official app stores like the Google Play Store or the Apple App Store. Avoid third-party app stores where malicious apps can slip through. - Review App Permissions:
Regularly check the permissions requested by your apps. If an app asks for access to your camera, microphone, or location without a clear reason, consider it a red flag. - Keep Your Software Updated:
Regular software updates patch security vulnerabilities. Make sure your operating system and all apps are up to date. - Enable Security Features:
Use built-in security features such as biometric authentication and two-factor authentication. These features add an extra layer of protection against unauthorized access. - Regular Backups:
Frequently back up your important data. In case you need to perform a factory reset, having a recent backup can save you time and stress.
Security Software Recommendations
Below is a summary of some recommended security applications that can help protect your phone from spyware and other threats:
| Security App | Features | Platforms |
|---|---|---|
| Certo Mobile Security | Full disk scanning, high detection rate | Android |
| ProtectStar Anti-Spy | Memory + APK scan, real-time blocking | Android & iOS |
| iVerify Basic | Focused on memory analysis and threat hunting | iOS |
Using a reliable security app can significantly reduce your risk of spyware infection. These applications are designed to detect even the most advanced forms of spyware by monitoring for unusual activity and flagging suspicious processes.
Case Study: Sarah’s Experience
Sometimes real-life stories help bring these issues into perspective. Let’s take a closer look at Sarah’s experience with spyware on her phone.
What Happened to Sarah?
Sarah began noticing that her phone was behaving unusually. The battery, which normally lasted all day, started depleting rapidly. Apps that she frequently used began crashing unexpectedly, and she kept receiving intrusive pop-up ads from unknown sources. Concerned about these sudden changes, Sarah decided to investigate further.
Using the step-by-step methods outlined above, she first booted her phone into Safe Mode and reviewed the running processes. She discovered an unfamiliar app that had been installed without her knowledge. Sarah then ran a full scan using ProtectStar Anti-Spy, which confirmed her suspicions of a spyware infection.
What Sarah Learned and How You Can Prevent Similar Issues
Sarah’s experience is a reminder that spyware can target anyone, regardless of technical expertise. Here are some lessons from her experience:
- Stay Alert: Unusual behavior, like faster battery drain or frequent crashes, should not be ignored.
- Act Quickly: The sooner you investigate and remove potential spyware, the less damage it can cause.
- Use Trusted Tools: Rely on well-reviewed security apps to perform scans and help clean your device.
- Regular Maintenance: Periodically review your app permissions and running processes to catch any signs of infection early.
By learning from Sarah’s experience, you can take proactive steps to protect your privacy and ensure that your phone remains secure.
Conclusion and Next Steps
In today’s interconnected world, protecting your mobile device from spyware is not just a technical concern but a crucial part of maintaining personal privacy. We’ve explored the common signs of spyware infection, detailed methods for detecting and removing spyware, and provided preventive measures to safeguard your device against future threats.
Key Takeaways
- Recognize the Signs: Watch for unusual battery drain, unexpected pop-up ads, and app crashes.
- Act Promptly: Use both automated tools and manual techniques to identify and remove spyware.
- Prevent Future Infections: Keep your software updated, only download apps from trusted sources, and regularly review your device’s permissions.
- Learn from Real Stories: Sarah’s experience shows that even everyday users are at risk and that a few simple steps can make a big difference.
Call-to-Action
Your privacy and security are in your hands. Take a few minutes today to review your smartphone’s security settings, uninstall any suspicious apps, and run a thorough scan using a trusted security tool. For more detailed guidance and to stay updated on the latest mobile security tips, subscribe to our newsletter and join the conversation on our social media channels.
For additional insights and detailed methodologies, explore resources like the UCSB Spyware Research Report and ZDNet’s guide on detecting spyware. These sources offer deeper dives into the techniques used by advanced spyware and provide further reading for those interested in the technical aspects.
Remember, maintaining digital privacy requires ongoing vigilance. Regularly update your security practices, and never hesitate to seek professional help if you suspect your device has been compromised. Stay safe, keep your information secure, and take control of your digital life.
Final Thoughts
Spyware is a persistent threat that can infiltrate even the most carefully managed devices. However, by staying informed and following the step-by-step processes outlined in this guide, you can detect, remove, and prevent spyware effectively. Whether you’re an everyday smartphone user or someone who values personal privacy, these strategies offer a clear roadmap to protecting your device against hidden surveillance.
Be proactive about your mobile security. Revisit these steps periodically, update your security software, and always be on the lookout for any unusual behavior on your device. Your vigilance today can prevent major privacy breaches tomorrow.
For more comprehensive security solutions and expert tips on mobile protection, check out these trusted resources:
- ProtectStar Anti-Spy on Google Play
- Certo Mobile Security Insights
- Community Advice on Reddit
- Detailed Removal Techniques on UHD
Taking the time to understand how spyware works and how to remove it is an investment in your digital freedom and personal security. Follow this guide, spread the word among friends and family, and make informed choices about the apps and services you use. Together, we can build a safer digital environment for everyone.
By following these detailed steps and leveraging trusted tools and practices, you can protect your personal information and enjoy a secure mobile experience. Remember, your smartphone is an extension of your life—keeping it safe should always be a priority.
Stay secure, stay informed, and take charge of your digital privacy today.