Understanding Cloud Data Security Practices

Cloud data security is a big deal, especially now that everyone’s moving to the cloud. It’s not just about keeping your files safe; it’s about making sure your whole business is protected. Think of it like this: if your data gets compromised, it can mess up everything from customer trust to your bottom line. So, getting a handle on cloud security practices is super important.
Importance of Cloud Security
Cloud security is important because it protects your data and applications stored in the cloud from theft, leaks, and deletion. It’s not just about keeping hackers out; it’s also about making sure your own employees don’t accidentally mess things up. With more and more sensitive information being stored in the cloud, the stakes are higher than ever. If you don’t take security seriously, you could face some serious consequences, like fines, lawsuits, and a damaged reputation. Plus, customers are more likely to trust businesses that have a strong security posture.
Common Threats to Cloud Data
There are a bunch of different threats to watch out for when it comes to cloud data. Here are a few:
- Data breaches: Hackers getting into your systems and stealing sensitive information.
- Malware: Viruses and other nasty software that can infect your cloud environment.
- Insider threats: Employees (or former employees) who misuse their access to steal or damage data.
- Denial-of-service (DoS) attacks: Overwhelming your systems with traffic, making them unavailable to legitimate users.
- Misconfigurations: Mistakes in how your cloud resources are set up, which can create security holes.
It’s important to remember that cloud security is a shared responsibility. Your cloud provider will handle some aspects of security, but you’re still responsible for securing your own data and applications.
Regulatory Compliance Considerations
Depending on your industry and where your customers are located, you might need to comply with certain regulations. Here are a few examples:
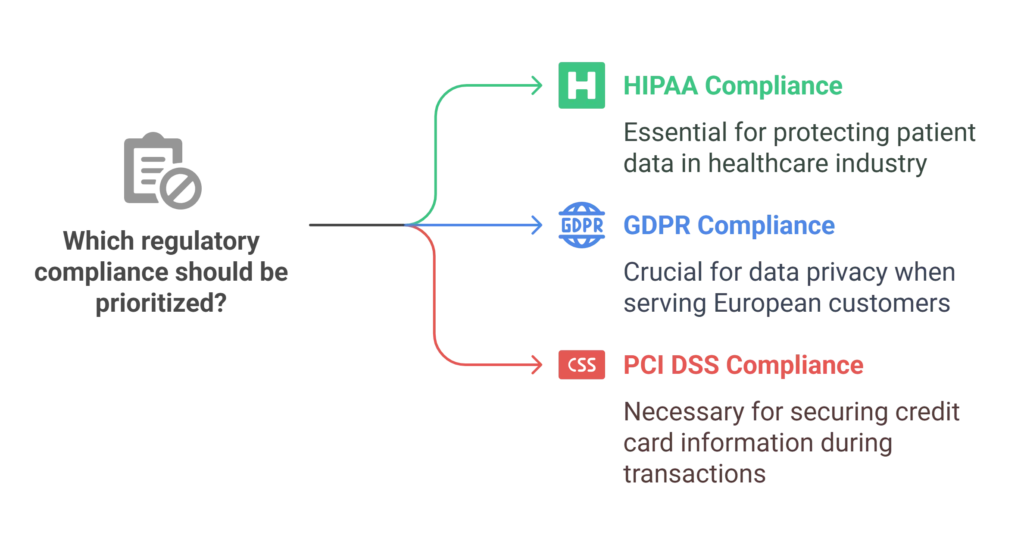
- HIPAA: If you’re in the healthcare industry, you need to protect patient data.
- GDPR: If you have customers in Europe, you need to comply with data privacy laws.
- PCI DSS: If you process credit card payments, you need to secure cardholder data.
It’s important to understand which regulations apply to your business and make sure your cloud security practices are up to par. Otherwise, you could face some hefty fines and other penalties.
Implementing a Zero-Trust Security Model
Defining Zero-Trust Principles
Okay, so you’ve probably heard the buzz about Zero-Trust. It’s not just a fancy term; it’s a whole new way of thinking about security. Instead of assuming everyone inside your network is trustworthy, you assume no one is. Every user, every device, every application needs to be verified before they get access to anything. Think of it like this: you wouldn’t just let a stranger into your house without checking who they are, right? Same idea here. This approach is especially important as more companies adopt cloud security strategy.
Benefits of Zero-Trust
Why bother with all this extra verification? Well, for starters, it seriously reduces the impact of breaches. If a bad actor manages to get inside, they won’t be able to move around freely. Zero-Trust limits their lateral movement, containing the damage. Plus, it gives you way better visibility into what’s happening on your network. You can see who’s trying to access what, and that helps you spot suspicious activity way faster. Here’s a quick rundown:
- Reduced breach impact
- Improved visibility
- Enhanced compliance
Steps to Implement Zero-Trust
Alright, so how do you actually make this happen? It’s not an overnight thing, but here’s a basic roadmap:
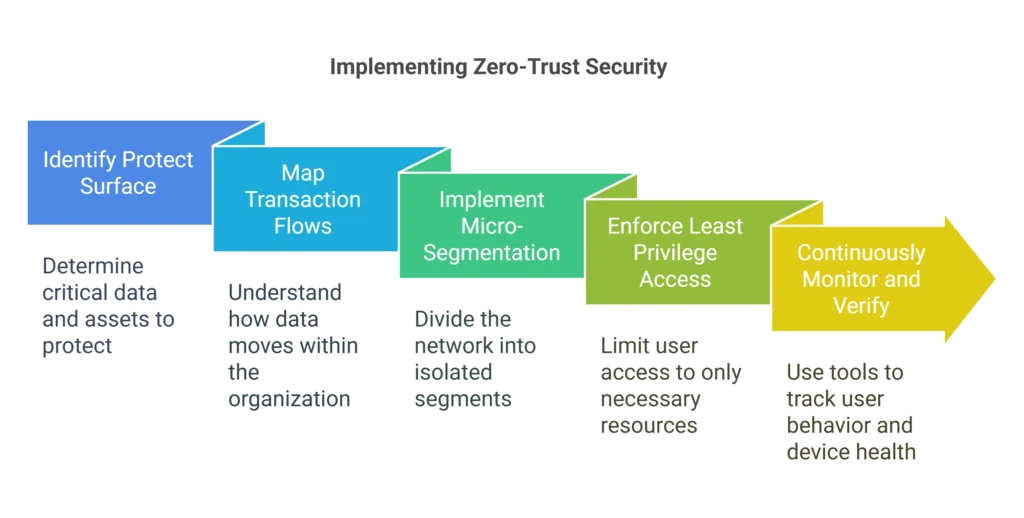
- Identify your protect surface: Figure out what data and assets are most important to protect. This helps you focus your efforts.
- Map the transaction flows: Understand how data moves around your organization. Who needs access to what, and when?
- Implement micro-segmentation: Divide your network into smaller, isolated segments. This limits the blast radius of any potential breach. You can limit public exposure to cloud resources.
- Enforce least privilege access: Give users only the access they absolutely need to do their jobs. Nothing more.
- Continuously monitor and verify: Keep an eye on user behavior and device health. Use tools like multi-factor authentication (MFA) and anomaly detection to spot anything suspicious. You can use conditional access policies to verify user identity.
Implementing Zero-Trust is a journey, not a destination. It requires a shift in mindset and a commitment to continuous improvement. But the payoff – a more secure and resilient cloud environment – is well worth the effort. Securing your smart home devices is a similar journey.
Data Encryption Strategies for Cloud Security
Data encryption is a cornerstone of cloud security. It’s not just about scrambling data; it’s about ensuring that even if a breach occurs, the information remains unreadable to unauthorized parties. Let’s explore some key strategies.
Encrypting Data at Rest
Data at rest refers to data that is stored, whether it’s in databases, file systems, or backups. Encrypting this data adds a layer of protection against physical theft or unauthorized access to storage devices. Think of it like putting your valuables in a safe; even if someone gets into your house, they still need the combination to get to the good stuff. You can use tools like AWS KMS or Azure Disk Encryption to protect stored information. It’s also critical to enforce regular encryption key rotations and protect those keys with Hardware Security Modules (HSMs).
- Use AES-256 encryption for databases and storage volumes.
- Implement key management strategies, including HSMs.
- Ensure compliance with regulations like GDPR and HIPAA.
Encrypting Data in Transit
Data in transit is data that’s being transferred between locations, whether it’s between your computer and the cloud, or between different cloud services. This is a particularly vulnerable point, as data can be intercepted during transmission. Imagine sending a postcard versus a sealed letter; the postcard’s contents are visible to anyone who handles it. To protect data in transit, use strong protocols like TLS 1.3. Supplement it with protocols like IPsec to secure VPNs and network traffic. Consider using SSH tunneling for encrypted communication between systems. This ensures that even if someone intercepts the data, they won’t be able to read it without the decryption key. It’s like sending your data in an armored car instead of a regular one.
- Use TLS 1.3 for web traffic.
- Implement VPNs with IPsec for secure network connections.
- Use SSH tunneling for encrypted communication between systems.
Key Management Best Practices
Encryption is only as strong as its key management. If your keys are compromised, your encrypted data is as good as unencrypted. Proper key management involves securely storing, rotating, and controlling access to encryption keys. Think of it like having a really strong lock, but leaving the key under the doormat. Here are some key considerations:
- Use Hardware Security Modules (HSMs) to protect encryption keys.
- Implement key rotation policies to minimize vulnerabilities.
- Control access to keys using the principle of least privilege. This is one of the cloud security practices that you should implement to keep your data safe.
Key management is often the most challenging aspect of encryption. It requires careful planning, robust processes, and the right tools to ensure that keys are protected throughout their lifecycle.
Identity and Access Management Essentials
Identity and Access Management (IAM) is super important for keeping your cloud data safe. It’s all about making sure only the right people have access to the right stuff. If you mess this up, you’re basically leaving the door wide open for attackers. Weak IAM practices are a huge problem, with many breaches linked to access permissions. Let’s get into the essentials.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a must-have. It adds an extra layer of security beyond just a password. Think of it like this: even if someone steals your password, they still need something else (like a code from your phone) to get in. It drastically reduces the risk of unauthorized access. For critical accounts, like admin roles, consider using non-phishable factors. It’s a simple step that can make a big difference. Make sure you enable IAM security for all cloud accounts, especially those with admin privileges.
- Enable MFA for all cloud accounts, especially admin accounts
- Inform users about the importance of MFA and offer guidance on how to use it
- Regularly review and update MFA settings to stay up to date with new standards
Principle of Least Privilege
The principle of least privilege means giving users only the access they absolutely need to do their jobs. Don’t give everyone admin rights just because it’s easier. This limits the damage if an account is compromised. It’s about being careful and intentional with permissions.
Implementing the principle of least privilege can be a bit of a pain at first, but it’s worth it in the long run. It reduces the attack surface and makes it harder for attackers to move around if they do get in. Think of it as containing the blast radius.
Regular Access Audits
Regularly auditing access is crucial. You need to check who has access to what and make sure it’s still appropriate. People change roles, projects end, and sometimes permissions just get forgotten. Audits help you clean up unused or unnecessary access, reducing the risk of someone exploiting those permissions. Here’s what you should do:
- Review user access rights at least quarterly.
- Revoke access immediately when an employee leaves or changes roles.
- Document all access changes and the reasons behind them.
Utilizing Cloud Access Security Brokers

Okay, so you’re probably wondering what a Cloud Access Security Broker (CASB) even is. Well, think of it as your cloud security guard. It sits between your users and your cloud apps, making sure everything is safe and sound. Let’s get into the details.
What is a CASB?
Basically, a CASB is a tool that helps you manage and secure your cloud usage. It acts as a gatekeeper, monitoring user activity and enforcing security policies across different cloud services. It’s like having a security checkpoint for all your cloud traffic. CASBs come in two main flavors: API-based and proxy-based. API-based CASBs integrate directly with cloud services, giving you visibility and control without disrupting traffic. Proxy-based CASBs, on the other hand, sit in the middle of the traffic flow, providing real-time control.
Benefits of Using CASBs
Why should you even bother with a CASB? Well, there are a bunch of good reasons:
- Data Loss Prevention (DLP): CASBs can prevent sensitive data from leaving your control. They can identify and block the transfer of confidential information, like credit card numbers or personal data.
- Shadow IT Discovery: Find out which cloud apps your employees are using without your permission. This helps you understand your risk exposure and bring those apps under control.
- Threat Protection: CASBs can detect and block threats like malware and phishing attacks in the cloud. They use various techniques, such as anomaly detection and threat intelligence, to identify and respond to suspicious activity.
- Compliance: CASBs help you meet regulatory requirements by monitoring and enforcing compliance policies. They can ensure that your data is stored and processed in accordance with regulations like GDPR or HIPAA.
Implementing a CASB can significantly improve your cloud security posture by providing visibility, control, and threat protection across your cloud environment. It’s a key component of a comprehensive cloud security strategy.
Choosing the Right CASB
Picking the right CASB can be tricky. Here’s what you should consider:
- Integration: Make sure the CASB integrates with your existing cloud services and security tools. You want it to work seamlessly with your current infrastructure.
- Features: Look for features that meet your specific needs, such as DLP, threat protection, and compliance monitoring. Think about what’s most important for your organization.
- Deployment: Decide whether you need an API-based or proxy-based CASB, or a combination of both. Consider your network architecture and security requirements.
- Scalability: Choose a CASB that can scale with your growing cloud usage. You don’t want to outgrow it in a year or two.
- Vendor Reputation: Research the vendor and read reviews to make sure they have a good track record. You want a reliable and trustworthy provider. Also, consider agentless vulnerability management to simplify the process of securing cloud environments.
Choosing the right CASB is a big decision, but it’s worth the effort. It can make a huge difference in your cloud security posture. Remember to consolidate your cloud security solutions for better efficiency and visibility.
Regular Security Assessments and Audits

Okay, so you’ve got your cloud setup, you’re feeling pretty good about your security measures. But here’s the thing: security isn’t a “set it and forget it” kind of deal. You need to be constantly checking and re-checking to make sure everything is still solid. That’s where regular security assessments and audits come in. Think of it as a health checkup for your cloud environment. Let’s get into it.
Conducting Vulnerability Assessments
Vulnerability assessments are all about finding the weak spots in your system before the bad guys do. It’s like hiring a team to try and break into your house, but instead of stealing your stuff, they tell you where you need to reinforce your doors and windows. You can use automated tools to scan your systems for known vulnerabilities, misconfigurations, and other potential problems. The goal is to identify and fix these issues before they can be exploited.
Here’s a quick rundown of what a vulnerability assessment might involve:
- Scanning your network and systems for open ports and services.
- Identifying outdated software and known vulnerabilities.
- Checking for misconfigured security settings.
- Analyzing the results and prioritizing remediation efforts.
Penetration Testing
Okay, so vulnerability assessments are like checking for unlocked doors. Penetration testing, or “pen testing,” is like actually trying to break in. It’s a more in-depth and hands-on approach to security testing. A pen tester will try to exploit vulnerabilities in your system to see how far they can get. This can help you identify weaknesses that automated tools might miss. It’s a good idea to conduct risk assessments regularly.
Here’s what a typical penetration test might look like:
- Reconnaissance: Gathering information about the target system.
- Scanning: Identifying open ports and services.
- Exploitation: Attempting to exploit vulnerabilities.
- Post-Exploitation: Seeing what the attacker can do once they’ve gained access.
- Reporting: Documenting the findings and recommending remediation steps.
Compliance Audits
Compliance audits are all about making sure you’re following the rules. Depending on your industry and the type of data you’re handling, you may be subject to various regulations and standards, such as HIPAA, PCI DSS, or GDPR. A compliance audit will assess your systems and processes to ensure that you’re meeting these requirements. It’s about cloud security practices and making sure you’re not going to get fined or penalized for non-compliance.
Think of compliance audits as a way to demonstrate to regulators and customers that you’re taking security seriously. It’s not just about avoiding fines; it’s about building trust and maintaining a good reputation.
Here are some things that might be checked during a compliance audit:
- Data encryption practices
- Access controls
- Incident response procedures
- Security policies and procedures
- Logging and monitoring practices
Continuous Monitoring and Incident Response
It’s not enough to just set up security measures and hope for the best. You need to keep a close eye on things and be ready to jump into action if something goes wrong. Think of it like having a home security system – it’s great to have, but it’s useless if you don’t monitor the alerts and respond when the alarm goes off.
Setting Up Monitoring Tools
You can’t fix what you can’t see, right? That’s why setting up the right monitoring tools is super important. We’re talking about tools that can track everything happening in your cloud environment, from user logins to data access and network traffic. The goal is to catch anything unusual before it turns into a full-blown security incident. Think of it as setting up security cameras all over your property. You’d want to see who’s coming and going, and if anyone’s acting suspicious.
- Deploy centralized logging solutions to collect logs from all cloud resources.
- Use SIEM tools for threat detection and event correlation.
- Ensure logs are stored securely and monitored for anomalies.
Incident Response Planning
Okay, so you’ve got your monitoring tools in place. Now what? You need a plan for what to do when those tools actually detect something. An incident response plan is like a fire drill for your cloud security. It outlines the steps you’ll take to contain, eradicate, and recover from a security incident.
- Create a multi-phase plan for detection, analysis, containment, and recovery.
- Integrate cloud-native services for real-time threat detection.
- Regularly conduct incident response drills to simulate realistic security breach scenarios.
A good incident response plan should include clear roles and responsibilities, escalation procedures, and communication protocols. Everyone on your team needs to know what they’re supposed to do in the event of a security incident.
Post-Incident Analysis
So, you had an incident, you responded, and hopefully, you contained the damage. But the work isn’t over yet! The post-incident analysis is where you figure out what went wrong and how to prevent it from happening again. It’s like doing an autopsy after a medical emergency – you want to understand what caused the problem so you can improve your procedures for the future. This also helps with regulatory compliance.
- Identify the root cause of the incident.
- Document the incident and the response.
- Update security policies and procedures based on the findings.
Wrapping It Up
In today’s world, where data is everything, keeping your cloud data safe is more than just a good idea—it’s a must. The tips we’ve covered here give you a solid starting point to protect your cloud setup from breaches and unauthorized access. Whether it’s about encrypting your data, managing who gets in, or keeping an eye on things for any weak spots, every little bit helps build a stronger cloud environment. Just remember, securing your cloud isn’t a one-time deal. As new threats pop up, you need to stay on your toes and update your strategies to keep everything secure.
Frequently Asked Questions
What is cloud security and why is it important?
Cloud security protects sensitive data and systems stored online from cyber threats. It is crucial because it helps prevent data breaches and builds trust with customers.
What are some common threats to cloud data?
Common threats include data breaches, insider threats, and account hijacking. These can lead to unauthorized access and data loss.
What does a Zero-Trust security model mean?
A Zero-Trust model means that no user or device is trusted by default, even if they are inside the network. Every access request must be verified.
How can I ensure my data is encrypted in the cloud?
You can encrypt data at rest (stored data) and in transit (data being sent) using strong encryption methods like AES for storage and TLS for transmission.
What is Multi-Factor Authentication (MFA) and why should I use it?
MFA adds an extra layer of security by requiring more than one form of verification to access accounts, making it harder for unauthorized users to gain access.
How often should I conduct security audits for my cloud systems?
It’s best to conduct security audits regularly, at least once a year, or whenever there are major changes to your systems or data.