The rise of quantum computing has opened up new opportunities and challenges for security. As traditional encryption methods become increasingly vulnerable, engineers and researchers have developed a new class of chips designed to protect data from quantum attacks. In this post, we explore how these cutting-edge defense chips work, their key features, and the many sectors that stand to benefit. We also highlight real-world applications, address deployment challenges, and look ahead to future advancements.
Understanding Quantum Threats and the Need for Defense Chips
Quantum computers work on the principles of quantum mechanics, and do calculations far beyond the capacity of conventional machines. However, it also brings a great threat to the encryption methods that are used to secure our digital communications, while this offer vast potential in optimization and material science.
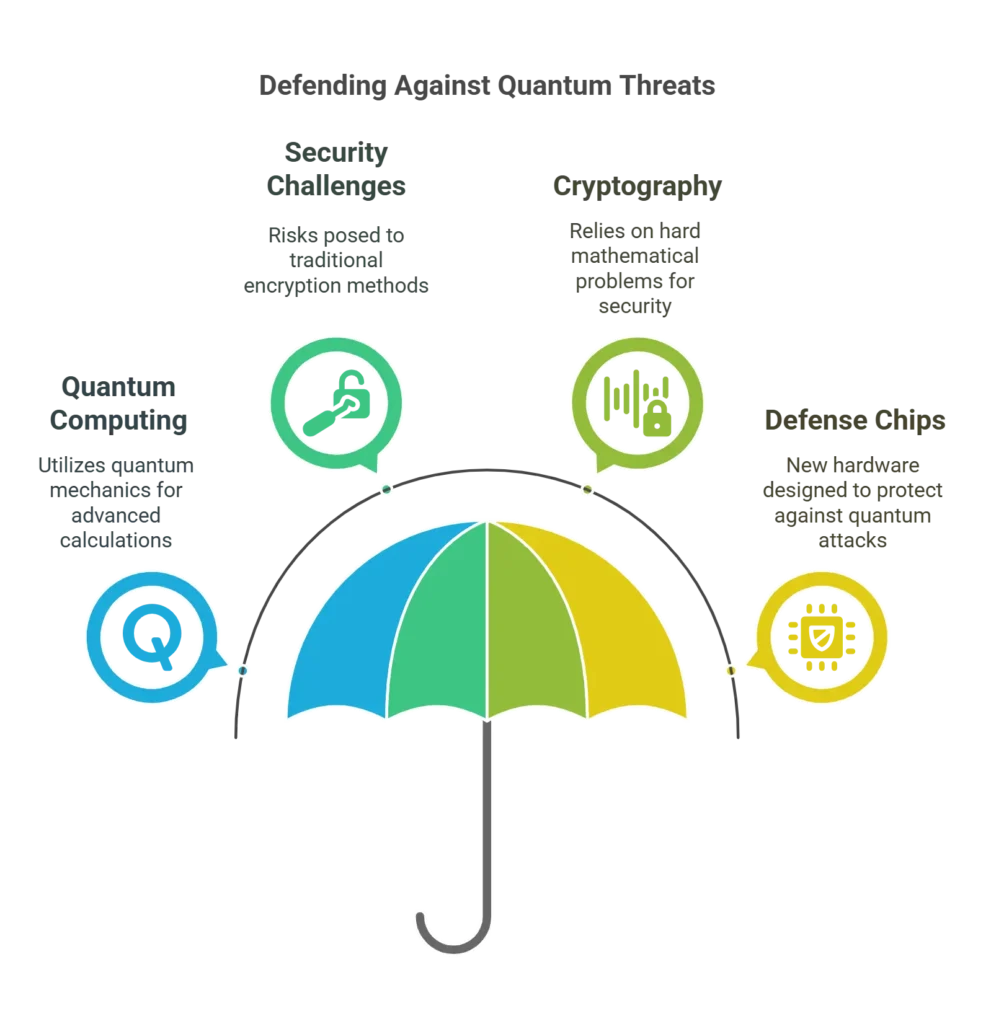
The Rise of Quantum Computing and Security Challenges
Traditional cryptography relies on mathematical problems that are hard for classical computers to solve. However, quantum computers can exploit algorithms—such as Shor’s algorithm—to break these problems much faster. This creates an urgent need for new hardware solutions that can defend against these threats. The world’s first quantum-attack defense chips are being designed to withstand attacks from both current and future quantum computers, ensuring that sensitive data remains secure.
What is a Quantum-Attack Defense Chip?

At its core, a quantum-attack defense chip combines advanced hardware features with next-generation cryptographic algorithms. These chips use built-in security measures that are hard-wired into the device, making them more robust against attacks. For instance, some designs incorporate Physical Unclonable Functions (PUFs) to generate unique keys directly from the manufacturing process. This approach not only reduces the risk of key extraction but also offers a dynamic root-of-trust that adapts during operation.
Key Innovations in Quantum-Attack Defense Chips
Recent breakthroughs in chip design have resulted in several innovative features that protect against quantum attacks. Below, we highlight some of the most significant advancements driving this technology forward.
Hardware-Rooted Trust and PUF Technology
One standout innovation is the use of PUF technology. Unlike conventional key storage, PUFs generate keys based on tiny, inherent variations in the silicon used during manufacturing. This means that each chip has a unique “fingerprint” that is nearly impossible to replicate. For example, New Electronics explains how Jmem Tek’s quantum-secure RISC-V chip leverages PUFs to provide a robust, hardware-based root-of-trust. By embedding security into the hardware, these chips avoid vulnerabilities associated with software-based key storage and help prevent unauthorized access.
Modular Quantum Processors and Reconfigurable Routing
Another innovative approach involves modular processor design. Researchers at the University of Chicago have introduced a chip design that replaces traditional fixed qubit grids with a flexible router hub. This architecture clusters qubits around a central switch, which enables dynamic reconfiguration of connections. As a result, the chip can adjust its configuration on the fly, ensuring that error correction and fault tolerance are maintained without sacrificing performance. This adaptable design makes the technology suitable for both edge devices and large-scale quantum computers. For more details on this design, visit the University of Chicago’s research page.
Hybrid Cryptography and Noise Injection Techniques
To provide strong protection against quantum attacks, these chips often combine classical and post-quantum cryptographic methods. SEALSQ’s QS7001 chip, for instance, integrates NIST-approved post-quantum algorithms like Kyber for key encapsulation and Dilithium for digital signatures along with classical protocols such as ECC‑256 and SHA‑256. This hybrid approach ensures backward compatibility while securing future communications. A New Electronics article details how this combination reduces cryptographic latency dramatically—from 1,500 ms to just 100 ms—thereby shrinking the window of opportunity for attackers.
Another intriguing method is quantum noise injection, developed by researchers at the University of Texas at Dallas. By purposefully introducing controlled noise into quantum circuits, this technique makes it difficult for adversaries to execute gradient-based optimization attacks. This means that even if an attacker tries to manipulate the system, the built-in noise obscures the true signal, adding an extra layer of protection. For further reading, check out the insights shared on the UT Dallas news site.
Real-World Applications and Sector-Specific Benefits
The design and deployment of quantum-attack defense chips have significant implications across various industries. Let’s take a closer look at some of the key sectors that can benefit from these innovations.
IoT and Edge Device Security
The Internet of Things (IoT) has connected millions of devices worldwide—from smart meters and industrial sensors to wearable health monitors. Many of these devices are resource-constrained and cannot support heavy cryptographic operations. By embedding PUF-based identity and lightweight cryptographic protocols, quantum-attack defense chips enable seamless, secure device onboarding and communication without adding extra hardware overhead.

For instance, Jmem Tek’s chip integrates with microcontrollers to provide secure provisioning and real-time security monitoring. This ensures that IoT ecosystems are better protected against potential quantum attacks, preserving data integrity and privacy in smart cities and industrial networks.
Financial and Payment Systems
Financial institutions are prime targets for cyberattacks due to the sensitive nature of their data. With traditional cryptographic systems at risk from quantum computers, banks and payment processors need robust defenses. Quantum-attack defense chips offer a solution by enabling secure transaction signing and preventing harvest-now-decrypt-later attacks. The reduced latency of these chips aligns with the strict real-time requirements of systems such as PCI‑DSS, ensuring that financial transactions remain both secure and efficient.
Military and Government Communications
National security and military operations depend on secure communications. A breach in military-grade encryption could have far-reaching consequences. Recent reports, such as those published by The Quantum Insider, highlight the potential for quantum computers to break existing encryption protocols used in military applications. With quantum-attack defense chips, sensitive communications can be safeguarded against these evolving threats. The adaptable designs and built-in hardware security make these chips suitable for battlefield-deployable secure networks and government infrastructure.
Comparative Overview of Quantum-Attack Defense Chips
Below is a table summarizing the key features and applications of several leading quantum-attack defense chips:
| Chip/Platform | Key Features | Cryptographic Approach | Target Applications |
|---|---|---|---|
| Jmem Tek’s Quantum-Secure RISC‑V Chip | PUF-based key generation, integration with Andes Technology’s N25F RISC‑V processor | Hardware-rooted security with dynamic key generation | IoT, industrial sensors, smart devices |
| SEALSQ’s QS7001 Chip | Hybrid encryption model, hardware acceleration, low cryptographic latency | Combination of Kyber, Dilithium with ECC‑256 and SHA‑256 protocols | Automotive IoT, financial transactions, secure networks |
| Microsoft Majorana 1 Chip | Topological qubits with significant error reduction, potential for on-chip QKD integration | Advanced error correction integrated with quantum-resistant schemes | Future quantum systems, large-scale secure data centers |
This table highlights the diversity of approaches in the field. Each chip is tailored to meet specific needs while ensuring that the overall system remains secure against both current and anticipated quantum threats.
Challenges and Deployment Considerations
While the promise of quantum-attack defense chips is significant, their deployment comes with challenges. Addressing these issues is key to ensuring that the technology can be adopted widely and seamlessly integrated into existing systems.

Performance Overheads and Hardware Constraints
One of the primary challenges is the trade-off between security and performance. Advanced cryptographic algorithms—especially those based on lattice cryptography—often require more computational resources. For example, lattice operations in post-quantum schemes can use several times the processing cycles compared to traditional algorithms. Engineers have been working to mitigate these overheads by integrating custom extensions into RISC‑V processors and sharing resources between classical and post-quantum components.
Interoperability and Hybridization Risks
Integrating new quantum-resistant methods with existing systems is not without risk. Combining classical protocols with post-quantum cryptography may introduce new vulnerabilities if not carefully managed. Downgrade attack vectors, where an attacker forces a system to revert to a less secure protocol, remain a concern. Chip designers are actively working on strategies, such as cascaded key derivation functions (KDFs), which derive keys simultaneously from both classical and quantum-resistant algorithms. This helps ensure that if one layer is compromised, the overall security remains intact. More on these challenges can be found in a detailed Secure-IC blog post.
Addressing Side-Channel Vulnerabilities
Side-channel attacks, which exploit indirect information such as power consumption and timing, are another challenge. In post-quantum systems, measures like masked arithmetic and randomized blinding are used to counter these threats. Although these countermeasures can introduce additional latency, ongoing research aims to refine these techniques to maintain a balance between security and performance.
Future Directions in Quantum-Resistant Security
Looking ahead, the development of quantum-attack defense chips is set to accelerate as industry collaboration and standardization efforts increase. Here are some of the promising directions for the future:
Integration with Quantum AI and Machine Learning
Emerging trends suggest that future defense chips may incorporate machine learning capabilities to optimize their security parameters in real time. By analyzing threat patterns and adjusting encryption settings on the fly, these chips can offer adaptive protection against evolving attack strategies. Researchers are experimenting with integrating reinforcement learning models to fine-tune quantum noise injection parameters, ensuring that security measures remain robust without manual intervention.
Standardization Efforts and Collaborative Frameworks
One of the hurdles for widespread adoption is the lack of uniform standards. Organizations like NIST are actively working on draft standards for post-quantum algorithms, while initiatives in the EU and efforts from industry bodies aim to create cohesive frameworks. Collaborative projects and working groups are helping to align the various approaches, ensuring that different systems can interoperate securely. For more on these collaborative efforts, the Infosecurity Magazine provides an excellent overview of current trends.
Wrapping Up and Taking the Next Step
The development of the world’s first quantum-attack defense chips represents a significant step forward in protecting our digital world. These chips combine hardware-rooted trust, adaptable processing architectures, and hybrid cryptographic approaches to offer a new level of security. Their applications span from securing everyday IoT devices to protecting sensitive financial and military communications.
For tech professionals, agencies, and companies alike, staying informed about these innovations is essential. Whether you’re responsible for securing an entire enterprise network or simply interested in the future of cybersecurity, understanding these advancements can help you prepare for a rapidly shifting threat landscape.
As quantum computing continues to advance, so too will the measures we take to protect our data. The journey toward robust quantum-resistant security is ongoing, and participation in standardization efforts and industry collaborations will be key to success. For more detailed insights on specific chip designs and research initiatives, explore the following resources:
- Jmem Tek’s quantum secure RISC‑V chip
- SEALSQ’s QS7001 platform for IoT security
- Chinese researchers’ demonstration of quantum hacking techniques
- Microsoft’s progress in quantum chip encryption
- University of Chicago’s novel chip design
- UT Dallas research on quantum computer attacks
- Insights on integrating post-quantum cryptography
By engaging with these sources and keeping an eye on emerging trends, you can be better prepared for the future of digital security.
Additional Insights: Practical Considerations for Deployment
For organizations planning to upgrade their security infrastructure, practical considerations must be taken into account. Implementing quantum-attack defense chips is not just about hardware—it also involves rethinking system architectures, updating protocols, and ensuring that new technologies integrate smoothly with legacy systems.
Evaluating Your Security Landscape
Before integrating a new defense chip, companies should assess their current security measures and identify vulnerabilities that could be exploited by quantum attacks. This evaluation should consider:
- Data Sensitivity: What types of data are at risk, and how critical is their protection?
- Existing Protocols: How well do current encryption methods stand up to emerging quantum techniques?
- Hardware Capabilities: Are current devices capable of supporting additional security measures, or will upgrades be necessary?
Implementation Roadmap
A structured implementation plan can help ease the transition. Here’s a simple roadmap for companies considering a shift to quantum-resistant security:
- Assessment: Conduct a thorough review of existing security systems and potential vulnerabilities.
- Pilot Testing: Deploy defense chips in a controlled environment to evaluate performance and compatibility.
- Integration: Roll out the chips in phases, ensuring that each stage of the deployment is closely monitored.
- Continuous Monitoring: Implement real-time monitoring solutions to track the effectiveness of the new security measures.
- Feedback and Adjustment: Use insights gained during the rollout to refine the deployment strategy further.
Table: Deployment Considerations and Benefits
| Consideration | Details | Benefit |
|---|---|---|
| Security Assessment | Identify critical vulnerabilities and data sensitivity levels | Targeted upgrades and reduced risk exposure |
| Pilot Testing | Deploy chips in a controlled environment to assess performance | Early detection of issues and fine-tuning of protocols |
| Integration Strategy | Phased implementation with continuous monitoring | Smooth transition with minimal disruption |
| Real-Time Monitoring | Use of advanced monitoring tools to track chip performance and security metrics | Proactive response to potential threats |
| Feedback Mechanism | Regular review and adjustment based on performance data | Ongoing improvements and long-term security enhancements |
This table can serve as a guide for decision-makers looking to understand the practical side of deploying quantum-attack defense chips.
Final Thoughts
Quantum-attack defense chips are not only a reaction to the appearing risks, it is a sign of the progression in the protection of the cyber world. Such chips provide a strategic approach to securing important systems and data by combining hardware security with the latest cryptographic approaches. Thus, these chips are designed to assist organizations in protecting their critical infrastructure and information against the upcoming threats.
Quantum-attack defense chips are not only a reaction to the appearing risks, it is a sign of the progression in the protection of the cyber world. Such chips provide a strategic approach to securing important systems and data by combining hardware security with the latest cryptographic approaches. These chips are the future of cybersecurity.
Although the road ahead may be complex, organizations can navigate the evolving landscape of cybersecurity with confidence by taking a measured and informed approach. There is a clear path forward whether you are exploring new ways to protect IoT devices or trying to secure sensitive financial transactions by embracing the new advancements in quantum-attack defense chips.
If you want to know more about how this technology can be incorporated into your security plan or if you have questions about its real-life use—please don’t hesitate to contact us or find out more using the extensive resources provided below this post. It is crucial to stay aware and flexible, as the rate at which quantum computing is changing the world of cybersecurity, it is crucial to stay up-to-date.
Here is how you can ensure your organization is prepared for the future by understanding the innovations behind quantum-attack defense chips, assessing your current security needs and preparing for future developments. This is an opportunity to update your cybersecurity strategy and make sure your data is protected against the quantum threats of the future.
For anyone – a technology leader, an agency decision-maker, or a professional in the tech industry – the future of secure communication is here. Stay connected, keep exploring industry developments, and see how these advanced defense chips could possibly fit into your overall security framework.
This post gives a full scale review of how the new developments in quantum-attack defense chips are changing the world of cybersecurity. These chips offer strong protection across various industries with hardware-rooted security measures, dynamic processor designs and hybrid cryptographic solutions. When reviewing the research and exploring real-world applications, consider the impact on your organization’s digital safety and ways to incorporate these advancements into your long-term strategy.
Don’t hesitate to share your thoughts, questions or concerns, or to connect with like minded industry experts to find out more about the exciting developments in quantum resistant security. This conversation about keeping our digital future secure is only just beginning and your input can play a big role in helping advance this important cause.
In the modern world, which is characterized by a very high rate of technological development, the protection against cyber threats is possible only by using new tools and concepts. The first quantum-attack defense chips are one of the most significant breakthroughs in this regard. These chips are the first of their kind to offer real-time protection against quantum cyber threats, with potential applications in IoT security, financial systems, and secure communications, among others.
Please take a moment to review the linked resources and give thought to how the integration of such innovative hardware solutions could benefit your organization. Whether you are involved in setting security standards or managing the day to day operations of a tech enterprise, the insights presented here are intended to educate and encourage you as you work toward a quantum secure future.
Incorporating these advanced solutions into your strategy and thinking about how to implement them for adoption will help companies and tech professionals to make sure that they are not only responding to the threats of today but also to the threats of the future. The initiative to secure communications in the quantum age has now begun, and you are invited to be part of the movement that will shape the next chapter of cybersecurity.